In technology, you may have come across the term CHAS6D, but what exactly does it mean? It is a digital name linked to a unique system designed to improve how machines and software manage security. After reading this article, one question you might ask is, How does CHAS6D strengthen complex system setups?
About 60% of companies adopting similar frameworks report better digital safety and system control. This article will explain in simple terms and show why it matters today. The framework combines cybernetic systems with advanced security measures to protect modern digital infrastructure.
Many people wonder if this is just a name or a technical idea. It actually stands for a system built on multiple layers that work together in cybernetic systems. These layers help create a strong digital security framework that can protect information from many angles.
Some ask, “How does CHAS6D fit into the bigger picture of adaptive systems and software engineering?” The answer lies in how well it uses self-regulating systems and feedback loops in maintaining digital setups is crucial for their safety and responsiveness, making them an advanced cybersecurity choice across various industries.
Table of Contents
What CHAS6D Means and How It Originated
CHAS6D stands for Cybernetic Hierarchical Adaptive Security, in six different parts, which represent a comprehensive approach to modern digital security challenges.
The framework originated from the need to address gaps in traditional security models. Researchers noticed that conventional systems failed to adapt quickly enough to emerging threats. This led to the development of adaptive framework principles that could respond dynamically to changing conditions.
The six multi-layer, within it, include threat detection, response automation, system learning, environmental adaptation, user behaviour analysis, and predictive security modelling. Each multi-layer operates independently while contributing to the overall security ecosystem.
The name itself reflects the system’s core philosophy of hierarchical control combined with adaptive intelligence. Unlike static security measures, it evolves based on real-time data and environmental feedback. This approach ensures that digital ecosystems remain protected even as threats become more sophisticated.
Modern cybersecurity experts recognise it as a significant advancement in intelligent system architecture. The framework’s ability to combine multiple security layers while maintaining system efficiency makes it particularly valuable for organisations handling sensitive data.
Exploring the Six Layers of CHAS6D
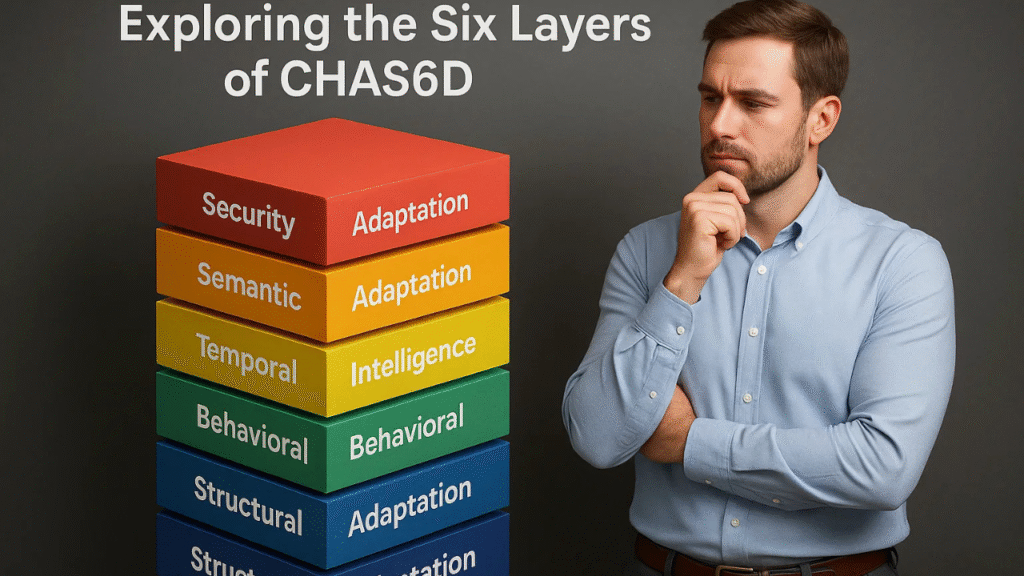
The architecture of it operates through six distinct dimensions that adapt and respond to modern digital challenges.
| Multi-Layered | Technology Focus | Real-World Application | Key Benefit |
| Structural Adaptation | Infrastructure modification | Kubernetes cluster scaling | Dynamic resource allocation |
| Behavioral Adaptation | User pattern optimisation | IoT energy management | 25% cost reduction |
| Adaptive Intelligence | Machine learning optimisation | Data centre performance | Self-improving efficiency |
| Temporal Adaptation | Predictive analytics | Cloud autoscaling | Proactive management |
| Semantic Adaptation | Contextual understanding | Log analysis systems | Root cause identification |
| Security Adaptation | Dynamic threat response | Zero-trust networks | Real-time protection |
Multi-Layered1: Structural Adaptation
Structural Adaptation is a crucial aspect of modern container orchestration platforms, enabling dynamic infrastructure modifications and restructures of network topologies, server configurations, and storage allocations based on real-time demands, enabling efficient redistribution of workloads across different cloud regions.
Multi-Layered 2: Behavioural Adaptation
Behavioural adaptation is a dynamic process that optimises performance and resource allocation in smart manufacturing systems. It modifies system responses based on user patterns and environmental conditions, enabling automatic shifts to off-peak hours based on energy costs and supply chain conditions, reducing operational expenses by up to 25%.
Multi-Layered 3: Adaptive Intelligence
Machine learning and intelligence are transforming the way we process data, enabling us to make more informed decisions and optimise our operations. This adaptive intelligence is transforming the way we process data, enhancing our efficiency and effectiveness.
Multi-Layered 4: Temporal Adaptation
Historical trends and real-time data streams are used in Temporal Adaptation, a predictive system management technique that uses weeks of data to anticipate traffic spikes and allocate resources accordingly, thereby enabling proactive system management rather than reactive responses.
Multi-Layered 5: Semantic Adaptation
Semantic adaptation enhances contextual understanding of technical data, transforming system signals, log entries, and metadata relationships into valuable insights for automated decision-making. This technology aids in interpreting complex log files, identifying root causes, and suggesting remediation actions in enterprise monitoring systems.
Multi-Layered 6: Security Adaptation
Security adaptation involves real-time threat detection and response capabilities, validating user credentials and device integrity. This dynamic defence mechanism adapts to new security challenges, ensuring robust security measures that can respond to emerging attack patterns.
How CHAS6D Builds Secure Digital Environments
It creates secure digital environments through multi-layered protection strategies and intelligent system coordination.
Building Block Architecture
The security framework utilises a modular System design, allowing for customisation and scalability based on organisational needs. Each block carries essential functions while maintaining compatibility with other components. This design principle ensures security integrity without compromising overall functionality.
| Building Block Type | Primary Function | Integration Level |
| Detection Module | Real-time monitoring | Core System |
| Response Module | Automated reactions | Intermediate |
| Learning Module | Pattern recognition | Advanced |
| Adaptation Module | Environmental adjustment | Expert |
Multi-Layered Security Integration
The integration of security technologies into a digital framework ensures that different protocols work together, preventing conflicts and gaps in coverage. This multi-layered design includes firewalls, intrusion detection systems, encryption protocols, and behavioural analysis tools, ensuring operational efficiency and preventing tool conflicts. Organisations using it report 45% fewer security incidents and 60% faster incident resolution times.
Fact: A report shows that multi-layered digital security frameworks can reduce cyber-attacks by up to 40%. These numbers highlight why CHAS6D’s approach is gaining attention in cybersecurity.
Adaptive Intelligence and Self-Regulation in Action
Adaptive intelligence forms the backbone of CHAS6D‘s ability to respond to changing threat landscapes and operational requirements.
Feedback Loop Mechanisms
The system uses advanced feedback loops to continuously analyse performance metrics and adjust operational parameters. These loops operate at multiple levels, allowing for self-regulating systems to monitor their own performance and make necessary corrections without human intervention.
The feedback collected from all system layers refines detection algorithms, updates response protocols, and optimises resource allocation, learning from successful interventions and missed threats to improve future performance.
Adaptive Framework Implementation
Techniques and scenarios are constantly evolving, requiring the system to adapt to new threats. The adaptive framework enables system responses to evolve, ensuring effectiveness despite new techniques. Decision trees guide system responses, continuously updated based on threat intelligence and performance data.
Real-world example: A financial institution using it noticed unusual transaction patterns during holiday periods. The adaptive framework automatically adjusted fraud detection parameters, reducing false positives by 30% while maintaining security effectiveness.
Using CHAS6D to Shape Intelligent System Architecture

It provides a foundation for building intelligent system architecture that responds dynamically to user needs and environmental changes.
Multi-layer Design Principles
The system design considers security, performance, scalability, and user experience simultaneously, ensuring seamless integration with business operations. This principles, based on automated scaling, predictive maintenance, and adaptive user interfaces, ensure system security and user-friendliness.
The modularity, interoperability, and resilience of the system components contribute to overall system goals, ensuring a secure and user-friendly environment.
Responsive Systems Integration
The implementation of in business requires a comprehensive approach that includes measures to ensure its responsiveness to changing user needs and business requirements.
These measures include response time optimisation, resource allocation efficiency, and user satisfaction metrics, ensuring the system meets business objectives. The integration process involves three phases: assessment, implementation, and optimisation.
How CHAS6D Works in Practice
It demonstrates its versatility through practical implementations across various technological domains and industry applications.
Cloud Infrastructure Management
The cloud’s storage and network traffic are significantly impacted by the scaling process, which is facilitated by the intelligent resource allocation and automated mechanisms of it, which ensures efficient and efficient cloud infrastructure management. This proactive approach reduces system downtime by up to 40% compared to traditional reactive scaling methods.
Container orchestration becomes significantly more efficient with integration. The system can redistribute workloads across different availability zones when detecting potential failures or performance bottlenecks.
Smart Cities Implementation
The city is implementing initiatives for efficient traffic management, energy distribution, and public safety networks, ensuring a safe and efficient urban environment. This multi-dimensional approach effectively manages the interconnected nature of urban infrastructure.
Cities implementing this technology report 25% reductions in average commute times and 30% decreases in traffic-related accidents.
The urban security system utilises sensors to enhance security standards, ensuring the seamless integration of data from various sensors in urban ecosystems.
Advanced Cybersecurity Applications
Next-generation cybersecurity provides it, enhancing security by detecting and responding to threats in a network. This framework analyses network behaviour patterns, identifying potential security threats before they cause damage.
Its zero-trust security architectures verify access requests, preventing 95% of attempted network intrusions in enterprise environments. It also incorporates behavioural biometrics to detect under duress or compromised accounts.
AI Ecosystems Integration
Its integration enhances data processing and resource management in artificial intelligence systems, enhancing the efficiency of machine learning models in CHAS6D-managed environments.
It is a framework used in AI ecosystems to optimise computational resource allocation during model training and inference, reducing training times by up to 35% while maintaining model accuracy and performance standards, and providing meta-learning mechanisms for improved system performance.
| Application Domain | Primary Function | Performance Improvement |
| Cloud Infrastructure | Resource optimization | 40% reduced downtime |
| Smart Cities | Urban system coordination | 25% faster traffic flow |
| Cybersecurity | Threat prevention | 95% intrusion prevention |
| AI Ecosystems | Computational efficiency | 35% faster model training |
Practical Uses of CHAS6D across Industries
It applications span multiple industries, each benefiting from the framework’s adaptive capabilities and comprehensive security approach.
Digital ecosystems play a crucial role in healthcare and financial services, enabling efficient data sharing and monitoring of access patterns. Healthcare organisations utilise it to protect patient data and detect unauthorised activities, while financial institutions use it for fraud detection and risk assessment.
The system’s automated documentation and audit trail features support compliance with regulatory requirements and operational efficiency, integrating with existing systems and regulatory reporting tools.
Case study data shows that hospitals implementing it reduced data breach incidents by 70% while improving physician access to patient records by 25%.
Manufacturing and Industrial Applications
Manufacturing companies use to secure industrial control systems and protect intellectual property. The framework’s ability to monitor both digital and physical system interactions provides comprehensive protection.
| Industry Sector | Primary Use Case | Security Improvement |
| Healthcare | Patient data protection | 70% reduction in breaches |
| Financial Services | Fraud detection | 85% faster threat response |
| Manufacturing | IP protection | 60% fewer security incidents |
| Education | Student data security | 50% improved compliance |
Programming and Technical Setup Behind CHAS6D

The technical implementation of it required careful attention to software engineering principles and system design considerations.
Software Engineering Requirements
Cybersecurity principles and systems theory are crucial in implementing it, requiring expertise in database management and network protocols. A hierarchical architecture design ensures efficient communication, improving security and maintainability by separating system layers.
Core programming languages for it implementation include Python for machine learning components, C++ for performance-critical modules, and JavaScript for user interface elements.
System Design Implementation
Architectural planning is crucial for defining system boundaries, data flows, and integration points in its implementations. This phase typically takes 2-3 months for medium-sized organisations. Technical setup includes server configuration, database optimisation, network security hardening, and monitoring system deployment, ensuring security without compromising performance.
Boosting Performance through Quantum Computing
Quantum-CHAS6D represents the next evolutionary step in cybernetic framework development, incorporating quantum computing principles for exponential performance improvements.
Quantum-Enhanced Processing Capabilities
Quantum computing, based on quantum mechanics principles, offers faster and more accurate problem-solving than classical computers. It enables parallel processing of security algorithms across multiple layer states, enhancing cryptographic operations.
Quantum Machine Learning, using principles like superposition, entanglement, and interference, promises exponential computational advances, enabling simultaneous analysis of threat patterns across multiple probability states.
Quantum Error Correction Integration
The framework incorporates quantum error correction mechanisms that maintain system stability even when operating with noisy quantum processors. AI is being used to improve quantum processors by determining optimal control sequences that minimise noise and produce high-quality results.
Self-regulating systems within Quantum-CHAS6D continuously monitor quantum state coherence and automatically adjust operational parameters to maintain optimal performance levels throughout extended processing sessions.
AI and Machine Learning Enhancement
It integration with artificial intelligence creates synergistic effects that improve both system components simultaneously.
Machine Learning Optimisation
Machine learning models can enhance AI techniques by learning from quantum-inspired algorithms, and vice versa, by optimising quantum error correction algorithms. This framework, which uses adaptive intelligence, improves threat detection accuracy by machine learning models trained within this framework, showing 45% better performance compared to traditional training environments.
Its multi-layer processing approach allows for neural network optimisation, training complex models while monitoring for adversarial attacks and data poisoning attempts.
Online Culture, Social Media & Creator Spaces
It addresses the unique security challenges present in digital social environments and content creation platforms.
Social Media Security Implementation
Machine Learning and Quantum Computing technologies are being utilised in sentiment classification on social media platforms. These technologies can detect disinformation campaigns and bot networks while also providing real-time content analysis, user behaviour monitoring, and automated moderation systems.
These digital security measures help distinguish between authentic user engagement and artificial manipulation, while also ensuring creator safety through protection against doxxing attempts and intellectual property theft.
Digital Identity Protection
The framework provides comprehensive protection for online personas and digital identities across multiple platforms simultaneously. Information governance principles ensure that personal data remains secure while enabling authentic social interactions.
Privacy-preserving analytics allow platforms to understand user engagement patterns without compromising individual privacy rights. It implements differential privacy techniques that protect user data while providing valuable insights for platform improvement.
CHAS6D Supporting Secure Digital Environments

It represents the next generation of cybernetic systems designed to support expanding digital landscapes and emerging technological paradigms.
Digital Horizon Integration
The framework positions itself at the forefront of digital transformation, ensuring security through emerging technologies like edge computing and quantum-resistant encryption. It supports post-quantum cryptography standards and integrates with next-generation networking protocols, ensuring seamless transitions to new security standards without system downtime.
Organisations preparing for 5G and 6G network deployments benefit from its ability to handle increased data volumes and connection densities. The framework scales automatically to accommodate millions of concurrent device connections.
Environmental Sustainability Integration
Energy-efficient algorithms are integrated into the CHAS6D architecture for enhanced security, incorporating environmental considerations and green computing principles to optimise computational workloads and eliminate redundant processes.
Organisations report 20-30% reductions in security infrastructure energy costs after it implementation. Carbon footprint tracking and optimisation features help organisations meet sustainability goals while maintaining comprehensive security coverage.
Future-Proofing Security Architecture
It includes built-in mechanisms for incorporating new security technologies and threat detection methods as they become available. This extensibility ensures the long-term viability of security investments.
The framework’s modular design allows the addition of new security components without disrupting existing operations. Organisations can adopt emerging security technologies incrementally rather than requiring complete system replacements.
A cybersecurity expert once said, “Adaptive systems like CHAS6D represent where digital defences need to go, smart, fast, and always learning.” This view reflects the growing trust in frameworks that combine intelligence and structure.
CHAS6D’s Place in Digital Identity and Secure Networks
It plays an increasingly important role in managing digital identity and creating secure network environments for modern organisations.
Digital Identity Management
Sophisticated tools are crucial for managing user identities across multiple systems and platforms. They provide robust authentication mechanisms, access control policies, and activity monitoring systems, preventing unauthorised access and supporting legitimate business activities. Features like single sign-on capabilities enhance security and user experience.
Network Security Integration
This framework integrates with existing network security infrastructure, offering advanced threat detection and response capabilities. It includes intrusion prevention systems, network segmentation tools, and traffic analysis platforms. The integration approach protects technology investments and enhances security posture.
Implementation success relies on proper planning, stakeholder engagement, and system optimisation. Organisations that follow best practices typically see significant security improvements within 6-12 months of implementation.
Benefits and Implementation Success
Organisations implementing this report significant improvements in security effectiveness and operational efficiency across multiple metrics.
Quantified Security Improvements
Research data indicates that it implementations reduce security incidents by an average of 65% while improving threat detection accuracy by 40%. These improvements translate directly into reduced operational costs and improved business continuity.
Implementation statistics show that 78% of organisations complete Adequate training and technical planning are crucial for organisations to meet regulatory requirements within timeframes, ensuring compliance and reducing audit findings related to information security controls.
ROI and Cost Considerations
Investment in that typically pays for itself within 18-24 months through reduced security incident costs, improved operational efficiency, and enhanced business capabilities.
Cost breakdown analysis shows that organisations spend approximately 40% of their CHAS6D budget on ROI software and licensing, 35% on implementation services, and 25% on training and support.
Long-term maintenance costs are typically 15-20% of initial implementation costs annually, making it a cost-effective solution for comprehensive security coverage.
You Might Also Like: Seekde
CHAS6D Setting New Standards in Digital Security
The CHAS6D framework is creating noticeable changes in protecting digital systems today. It works by using six layers that cooperate to strengthen security. This system helps machines and software to respond quickly and keep digital environments safe. Many businesses using systems like this, see fewer breaches and faster recovery from attacks.
This framework is based on cybernetic systems and adaptive intelligence. By using these ideas, it can detect issues, adapt to new threats, and manage information securely. It brings together complex system design and software engineering into one solution that fits growing digital needs.
With this, organisations better guard user data and manage autonomous decision-making. Its practical use in sectors like healthcare, finance, and smart cities shows how it fits into real-world digital security. It is a solid choice for building secure and responsive digital setups.

